Virtual machines have become an indispensable component of modern computing systems. Whether you’re seeking to host multiple web applications or you want to provide a more secure testing environment, virtual machines offer the ability to run multiple operating systems and manage system resources with much greater ease. To better understand this versatile technology, let’s explore the different types of virtual machines available and their distinctive purposes.
So, what is a virtual machine used for? And what is virtual machine technology capable of? One of the key functions of a virtual machine is its ability to emulate an entire computer system within another operating system. This technology gives users the ability to run various applications designed for specific operating systems on their own devices without having to reconfigure or alter the native setup. In these contexts, there are two main categories of virtual machines: system virtual machines and process virtual machines.
System virtual machines, colloquially known as hardware virtual machines, provide a complete and isolated environment that emulates all components of a physical computer – including memory, processor, input/output devices, and storage – within the host operating system (OS). This enables users to install and run multiple instances of different operating systems simultaneously on one machine while maintaining separate resources for each instance.
Process virtual machines, on the other hand, focus on running individual applications rather than emulating an entire system. These types of virtual machines are designed around specific programming languages or runtime environments (like Java or Python) and enable more substantial cross-platform compatibility for software written using these languages. By abstracting away platform-specific details, process virtual machines allow developers to create programs that can be executed seamlessly across diverse hardware configurations without any modifications.
Virtual Machine in OS
The concept of a virtual machine in OS has completely changed the way businesses, organizations, and individuals utilize their computing resources. This technology allows for greater flexibility, efficiency, and cost savings, as it reduces the need for dedicated hardware for each application or user.
One of the primary benefits of a virtual machine in OS is its ability to minimize hardware costs while maximizing resource utilization. As multiple operating systems can share resources on one physical machine, fewer devices are needed to accommodate various applications and users. This can lead to dramatic cost savings in terms of equipment purchases and maintenance, as well as reduced energy dependency.
There are several types of virtual machines in OS that cater to diverse needs and use cases. One common type is known as system-level virtualization, which includes fully isolated guest operating systems running on top of a host OS controlled by hypervisor software. Another prevalent type is process-level virtualization, which runs individual applications within isolated containers instead of full-fledged guest operating systems. These containerized environments share some components with their host OS but still maintain a level of separation.
Understanding these nuances becomes clearer when examining how they function through diagrams depicting the structure and layers involved in each type. In system-level virtualization diagrams often depict hypervisors managing guest operating systems running atop them – with each layer encapsulated beneath it representing distinct physical hardware components like processors, memory, storage devices, and so on.
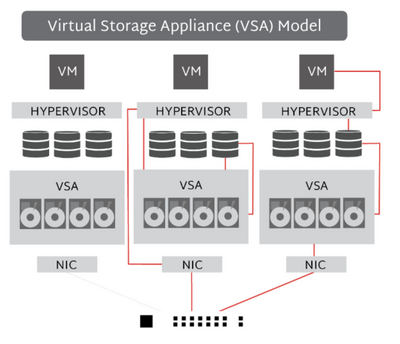
Benefits of virtual machines in OS for organizations and individuals by optimizing resource utilization, minimizing costs, and enhancing security features. With multiple types available to cater to various requirements, it is essential to understand the differences between system-level and process-level virtualization and how they function. Visualizing these concepts through diagrams helps in understanding the underlying principles that enable this technology to deliver its myriad advantages.
Virtual Machine in Cloud Computing
A virtual machine in cloud computing is a software-based representation of a physical computer that can run an operating system and applications, and perform tasks just like a traditional hardwired device. This technology allows multiple independent virtual machines to coexist on a single physical host while providing innumerable benefits to organizations and users alike.
Perhaps the crux of understanding what a virtual machine in cloud computing is, requires an examination of its functional components. These include an OS that functions as the primary interface between the user and the virtual machine, applications that provide specific capabilities or tools for users, and data that represent information processed or stored within the environment.
VMware, one of the leading providers of virtualization solutions, offers VMware Virtual Machine – a popular choice among businesses looking to benefit from cloud computing technology. This platform empowers organizations to create multiple isolated environments on a single physical server while maintaining control over resource allocation and management. This not only ensures efficient utilization of available resources but also minimizes any potential downtime as a result of hardware failure or maintenance activities.
System Virtual Machine vs Process Virtual Machine
System virtual machines and process virtual machines are two different types of virtualization technologies that have distinct applications and benefits. However, both of these technologies share the common goal of providing efficient, scalable, and secure computing environments for organizations and individual users.
A system virtual machine example generally refers to a hardware-level virtualization technology that allows multiple instances of an operating system to run concurrently on a single physical machine. This occurs when creating a virtualized environment that emulates the underlying hardware, isolating each virtual machine from one another.
Contrarily, process virtual machines operate at the application level and focus on executing specific programs within a secured environment. Process virtual machine examples may include Java Virtual Machine (JVM) and .NET Framework's Common Language Runtime (CLR). These platforms allow developers to write code once and deploy it across multiple operating systems without modification.
Process virtual machines offer several advantages which include platform independence, enhanced application performance, simplified software distribution, and robust security features. In comparing system virtual machine vs process virtual machine technologies, it is important to consider their respective use cases.
Both system and process virtual machines offer unique benefits in their respective domains – system VMs for consolidating infrastructure components while increasing efficiency in IT environments and process VMs for ensuring seamless interoperability across platforms in software development processes.
Types of Virtual Machine Software
Complete immersion in the digital world can sometimes involve the utilization of virtual machine software. This innovative technology allows for the creation and management of multiple operating systems within a single physical computer, unlocking a plethora of advantages for users, including heightened efficiency, security, and greater versatility.
With an extensive list of guest operating systems – ranging from Windows and Linux to Solaris – it offers immense flexibility for developers, testers, and IT administrators alike. Its strong community involvement ensures continuous enhancements in performance optimization.
Microsoft Hyper-V also merits attention when considering types of virtual machine software. Integrated into Windows Server in 2008, this hypervisor-based technology delivers high scalability and dynamic memory allocation – making it ideal for enterprise environments where resource management is crucial. It further boasts features like live migration and failover clustering – ensuring maximum uptime for critical workloads.
Exploring various types of virtual machine software will prove invaluable when seeking an optimal solution tailored to individual needs. Whether leveraging VMware Workstation Pro's power and stability, capitalizing on Oracle VM VirtualBox's open-source flexibility, Microsoft Hyper-V's enterprise-focused functionality, or Scale Computing HyperCore – the possibilities are endless in today's dynamic digital landscape.
As more organizations recognize the benefits derived from implementing these solutions – an upward trajectory in innovation can be anticipated in the realm of virtualization technology.
Hypervisor in Cloud Computing
Hypervisors in cloud computing have emerged as a revolutionary technology, enabling the efficient allocation of resources and management of multiple virtual machines within a single physical server. They play an integral role in optimizing resource usage, improving security and scalability, and reducing costs.
A primary advantage of using hypervisors in cloud computing is their ability to isolate different virtual machines from one another. This process not only bolsters security by preventing any potential threats or vulnerabilities from spreading across the system but also allows administrators to manage resources more effectively.
Another benefit of employing a hypervisor in cloud computing is its capability to be hardware-agnostic. This means that it can function irrespective of the underlying infrastructure upon which it's deployed. As a result, businesses have greater flexibility when choosing their hardware configurations and can avoid vendor lock-in while maximizing compatibility with various systems.
Ultimately, hypervisors play an indispensable role in modern-day cloud computing environments by enabling organizations to maximize resource utilization while maintaining security, scalability, and flexibility. Their ability to isolate virtual machines, support live migration, and facilitate disaster recovery efforts makes them a vital component for any company seeking to reap the many benefits of cloud computing.
Best Virtual Machine
In summation, understanding the myriad options in terms of virtual machines is crucial for making informed decisions in an increasingly virtualized world. Though there is no one-size-fits-all answer to the question of the best virtual machine, the choice will depend on specific use cases and requirements.
If you prioritize efficiency and performance, scalability, or compatibility with a particular operating system, Scale Computing HyperCore is based on a 64-bit, hardened and proven OS kernel, and leverages a mixture of patented proprietary and adapted open-source components for a truly hyperconverged product. All components—storage, virtualization, software, and hardware—interface directly through the HyperCore hypervisor and SCRIBE storage layers to create an ideal computing platform that can be deployed anywhere from the data center to the edge of the network.
The SC//HyperCore software layer is a lightweight, type 1 (bare metal) hypervisor that directly integrates into the OS kernel and leverages the virtualization offload capabilities provided by modern CPU architectures.
Specifically, SC//HyperCore is based on components of the Kernel-based Virtual Machine (KVM) hypervisor, which has been part of the Linux mainline kernel for many years and has been extensively field-proven in large-scale environments.
Ultimately, the best virtual machine example for your project will likely involve a combination of these technologies. By assessing your objectives and evaluating the strengths and advantages of various virtual machines, you can optimize your virtualization strategy to meet the demands of your IT environment, ensuring greater efficiency, reliability, and cost-effectiveness.